Hunting What Alerts Cannot See: Detecting Low-and-Slow Intrusions Through Behavioral Sequence Analysis
Threshold-based detection is optimized for noisy adversaries. Mature threat actors operate below every threshold, using legitimate tools, valid credentials, and normal-looking activity patterns that are individually benign but collectively constitute an intrusion. This essay examines why alert-driven SOCs systematically miss these campaigns, explains the hypothesis-driven hunting methodology that finds them, and evaluates which telemetry investments and analytical techniques actually produce results.
Cloud Control Plane Lateral Movement: How a Stolen Pod Token Becomes Full Account Compromise
In cloud-native breaches, the most consequential attacker actions happen not at the workload level but at the control plane , IAM, resource management, logging configuration, key management. Lateral movement through the control plane follows predictable patterns: credential harvesting from metadata services, IAM enumeration, role chaining, and privilege escalation through trust relationships. This essay traces these patterns through real incidents, explains why traditional network segmentation does not contain them, and evaluates the IAM architecture patterns that limit blast radius.
The Shrinking Window: CVE Disclosure to Mass Exploitation Is Now Measured in Hours
Empirical data from Log4Shell, ProxyLogon, MOVEit, and dozens of other critical vulnerabilities shows that the time between public CVE disclosure and active exploitation has collapsed from weeks to hours. This essay examines why, traces the specific timelines, and argues that the traditional patch-cycle model of vulnerability management is no longer viable for internet-facing systems.
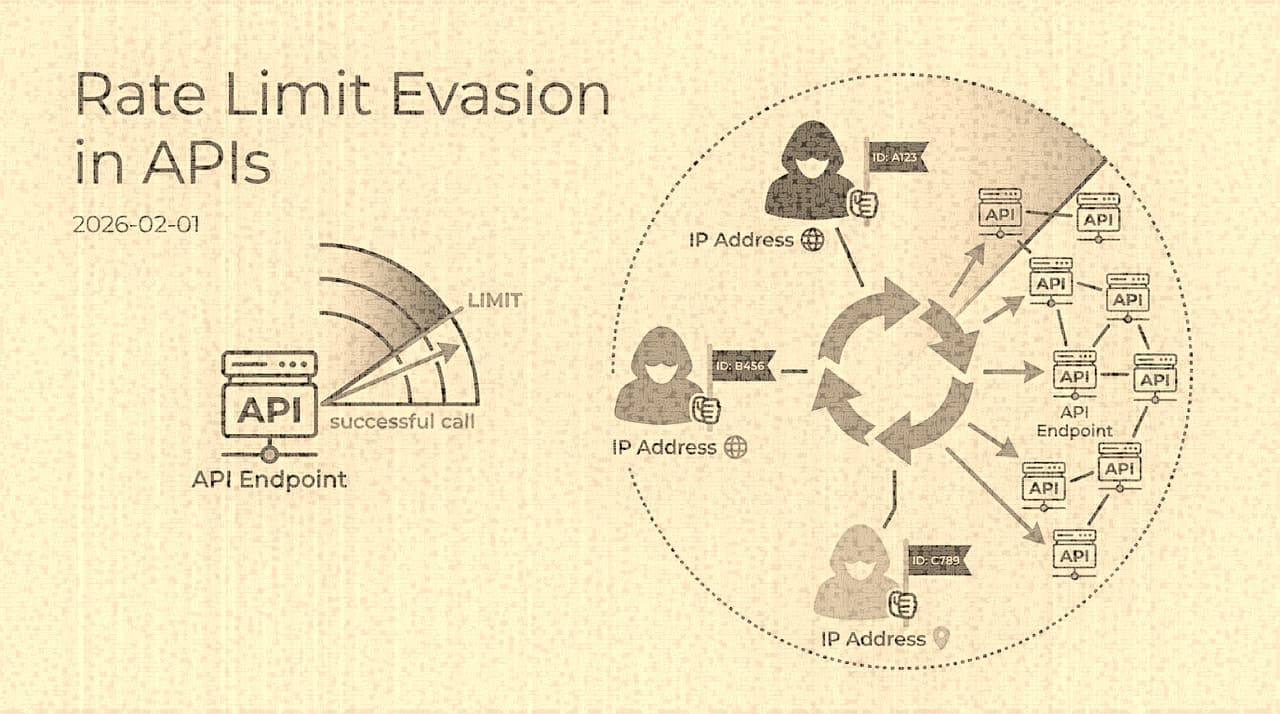
The Economics of API Abuse: Why Rate Limiting Fails and What Replaces It
API rate limiting, as typically implemented, is a volume control applied to a shape problem. Attackers who understand your throttling dimensions can stay below every threshold while still achieving their objectives at scale. This essay examines why threshold-based rate limiting systematically fails against modern distributed abuse, draws on real credential-stuffing economics, and argues for a shift toward intent-based abuse detection.
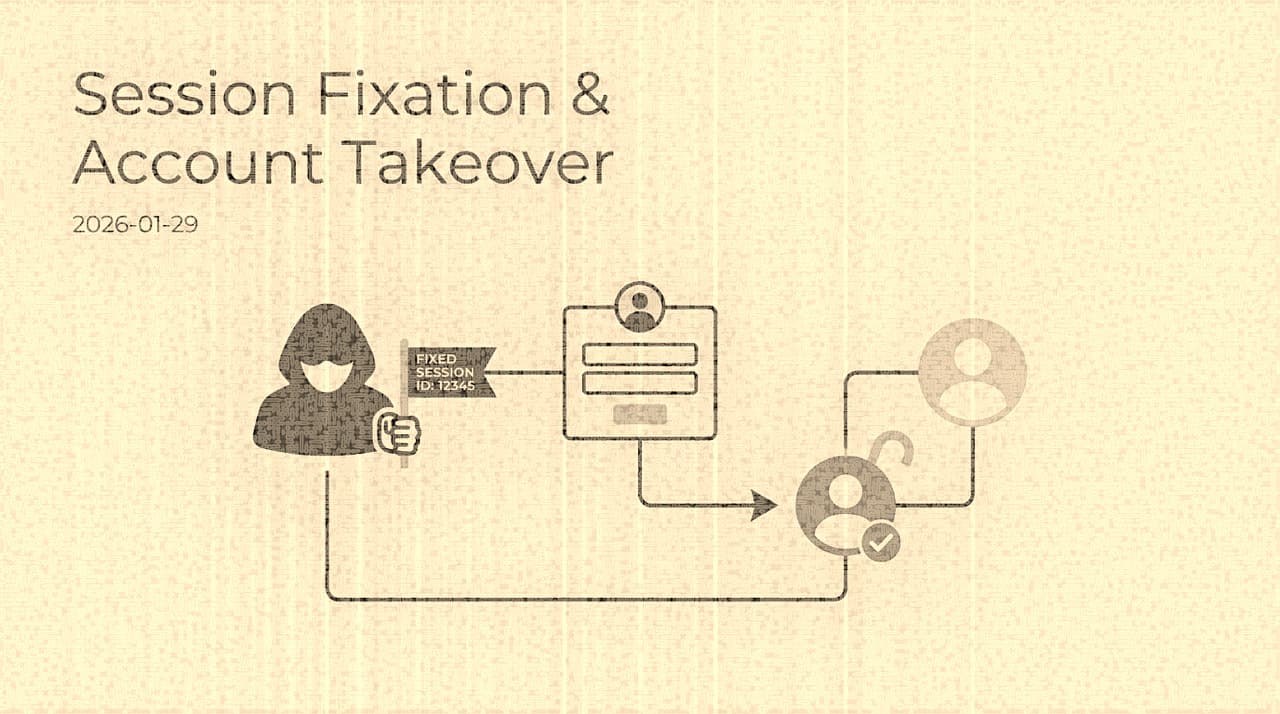
Session Fixation Is Not a Legacy Bug , It Is a Design-Level Failure in State Management
Session fixation bypasses authentication entirely by exploiting the gap between session identity and authentication state. Twenty years after the technique was formally described, it still surfaces in production because frameworks optimize for continuity, not for security transitions. This essay traces the structural reasons, examines real-world incidents, and argues that the fix requires treating session lifecycle as a first-class security primitive.
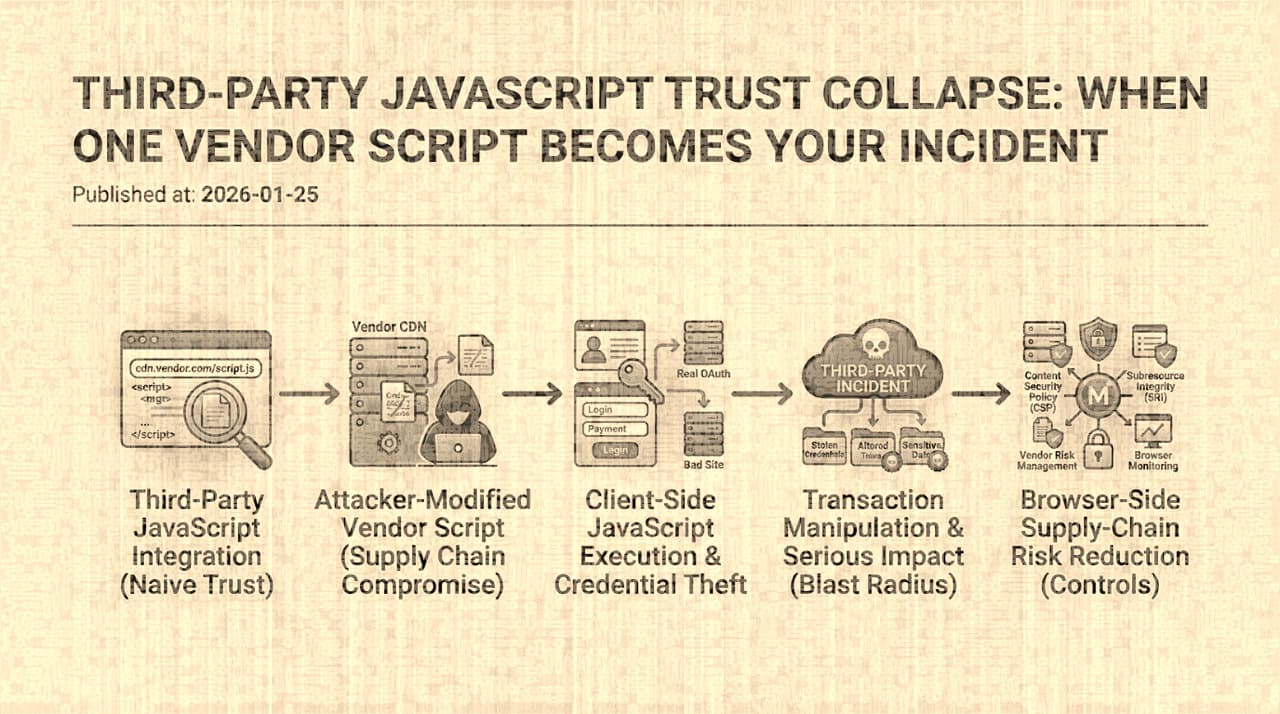
Third-Party JavaScript and the Collapse of Browser Trust: How One Vendor Script Becomes Your Incident
When you add a third-party script to your site, you are granting a company you do not control the ability to execute arbitrary code in your users' authenticated sessions. The British Airways and Magecart campaigns demonstrated what happens when that trust is violated at scale. This essay examines the structural trust problem, traces real-world supply chain compromises in the browser, and evaluates the architectural patterns , CSP, SRI, sandboxed iframes, and client-side telemetry , that actually limit the blast radius.
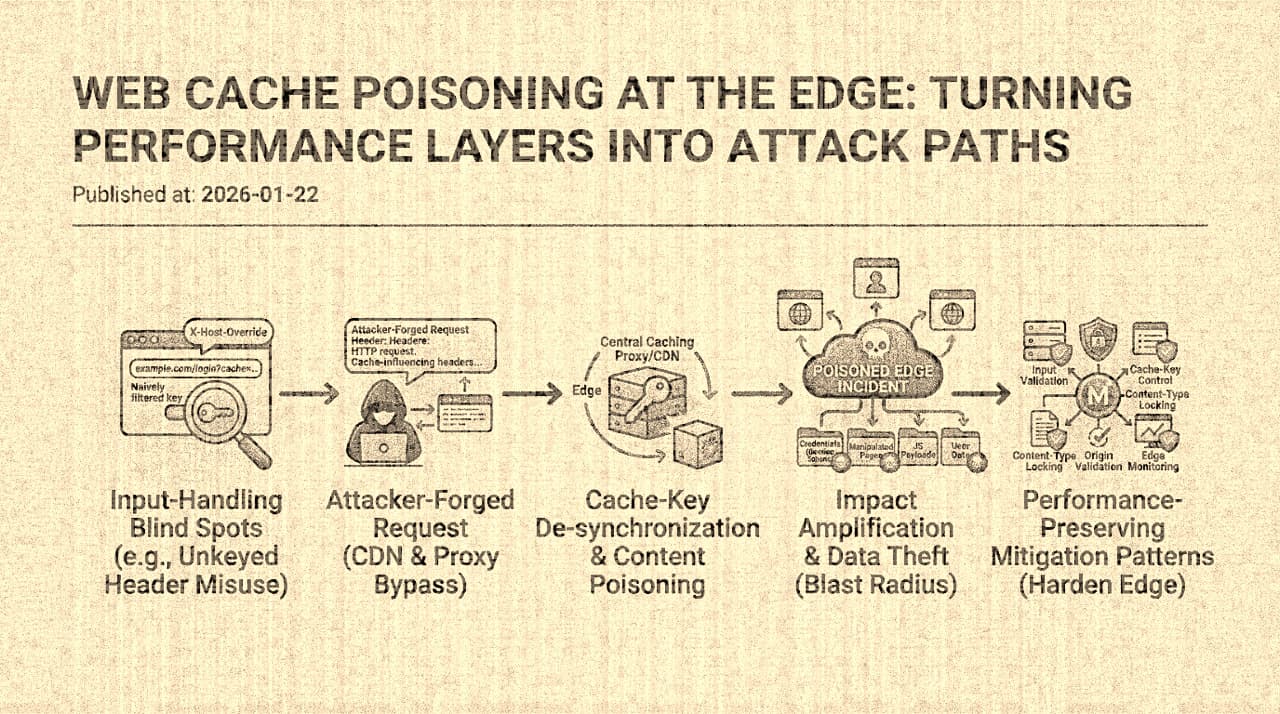
Web Cache Poisoning: How Performance Infrastructure Becomes an Attack Amplifier
Web cache poisoning occurs when an attacker injects content into a shared cache that is then served to other users, turning CDN infrastructure into a malicious content distribution network. The vulnerability class arises from the gap between what a cache considers to be the same request (the cache key) and what the origin considers to be different requests (the full request context). This essay examines the mechanics through James Kettle's foundational research, traces the specific CDN behaviors that enable poisoning, and evaluates the cache architecture patterns that prevent amplification.
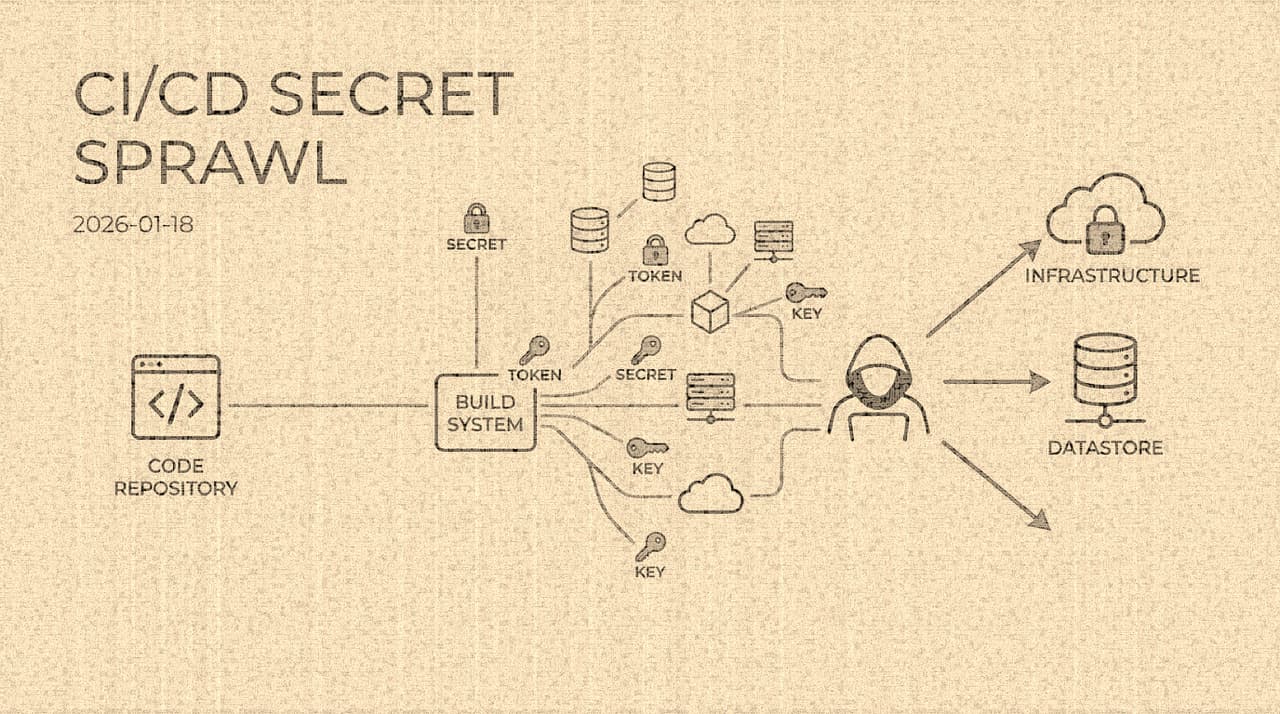
CI/CD as Crown Jewel: How Build Pipelines Became the Most Dangerous Systems in Your Organization
The Codecov, SolarWinds, and CircleCI breaches demonstrated the same structural truth: CI/CD pipelines hold more concentrated privilege than almost any other system in a modern organization, yet receive a fraction of the security scrutiny. This essay examines why secret sprawl in build infrastructure is not a hygiene problem but an architectural one, traces the common breach patterns, and evaluates the realistic effectiveness of mitigations from OIDC federation to ephemeral credentials.
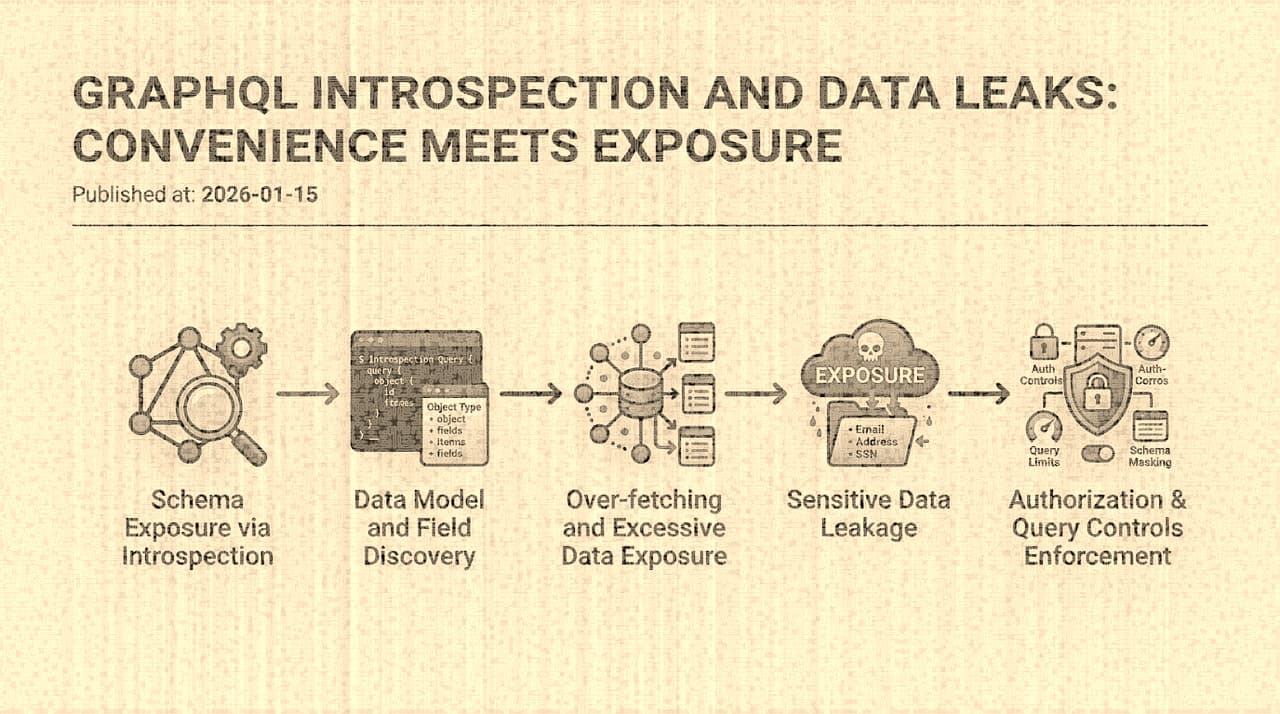
GraphQL's Security Model Is Inverted , And Most Teams Don't Realize It Until After the Breach
GraphQL APIs expose an unusually rich attack surface because they invert the typical API security model: instead of the server defining what data the client can access, the client specifies what it wants, and the server must enforce boundaries at every resolver. Introspection amplifies this by handing attackers a complete map of the data model. This essay examines why GraphQL's design makes authorization failures almost inevitable, traces real breach patterns, and evaluates the architectural changes that actually reduce risk.